Resources

Deciding between open-source and proprietary VoIP for your business
When selecting a Voice over Internet Protocol (VoIP) phone system, businesses often face a key decision: should they go with open-source or proprietary systems? This

Is your PC slowing down? Here’s why defragmentation still matters
If your Windows PC feels slower than it used to, fragmented files could be part of the problem. Learn how disk defragmentation works, when it’s

One login, total access: Why businesses are switching to single sign-on
Tired of managing endless passwords across your business apps? Single sign-on (SSO) offers a secure, streamlined solution that improves productivity while strengthening protection. Here’s why
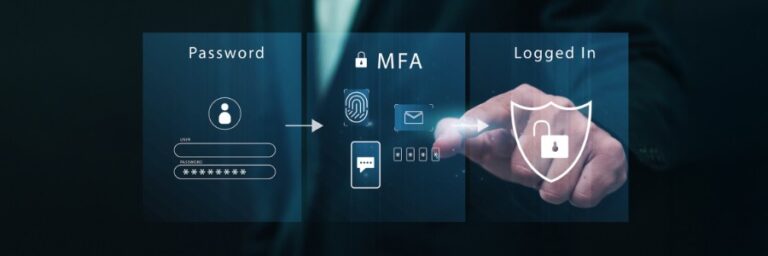
The hidden weaknesses of multifactor authentication
Multifactor authentication (MFA) works by requiring users to provide more than one form of identification when logging into a system or account. This extra layer

Questions to ask before upgrading your servers
Upgrading your company’s servers is a crucial decision that affects everything from operations to long-term growth. Rather than rushing into a replacement, it’s important to

Choosing between cloud and on-site VoIP hosting: A guide for businesses
With Voice over Internet Protocol (VoIP) becoming increasingly more common for businesses, business leaders must choose between cloud and on-premises hosting, both of which offer

Why Microsoft Whiteboard is becoming a go-to tool for team collaboration
With remote and hybrid work now the norm, visual collaboration tools have become essential for allowing teams to brainstorm, plan, and innovate together in real

Turning lookers into buyers: 5 Website tips for small businesses
Imagine a customer walking into your physical store, looking around for five seconds, and then immediately walking out without saying a word. The same thing

Defending against data loss: 6 Strategies businesses should implement
Cyberattacks, technical failures, or simple human error can creep up out of nowhere. And when they occur, businesses are often left scrambling to recover lost

2026 Cybersecurity trends and predictions
Cybersecurity experts Rob Wright (Dark Reading), David Jones (Cybersecurity Dive), and Alissa Irei (TechTarget Search Security) recently came together to discuss the future of online